
One of the best resources I’ve come across for anyone interested in cybersecurity and network traffic analysis is malware-traffic-analysis.net. This website hosts a vast collection of PCAP files containing captured traffic from compromised machines, along with exercises for those looking to sharpen their analysis skills. Studying this kind of real-world data provides valuable insight into the behaviors of different types of malware, from info stealers to botnets and worms.
Handling live malware samples, even passively through packet capture (PCAP) analysis, requires a secure and isolated environment. While a basic Kali Linux VM would be sufficient, I opted to leverage my Virtualized Cyber Lab for added protection, utilizing a pfSense firewall as an additional layer of defense. Security is only part of the equation—having access to external security tools such as VirusTotal is equally important for analyzing artifacts. If a full cyber lab isn’t available, a host-only network setup would be a safer alternative. That said, many of the malware samples analyzed from this resource primarily target Windows systems, making my Kali Linux VM immune to direct infection.
The samples available on malware-traffic-analysis.net provide a realistic representation of modern malware trends—which, as expected, means a heavy focus on information stealers. While these are useful for research, it’s always exciting when something more unique appears. One such case was highlighted in the blog post: "Malspam Pushing the Mydoom Worm is Still a Thing". Despite being over 11 years old as of this writing, Mydoom remains active in its spamming campaign. Examining the network traffic from an infected system, we can see malicious email (malspam) spreading the worm in action.
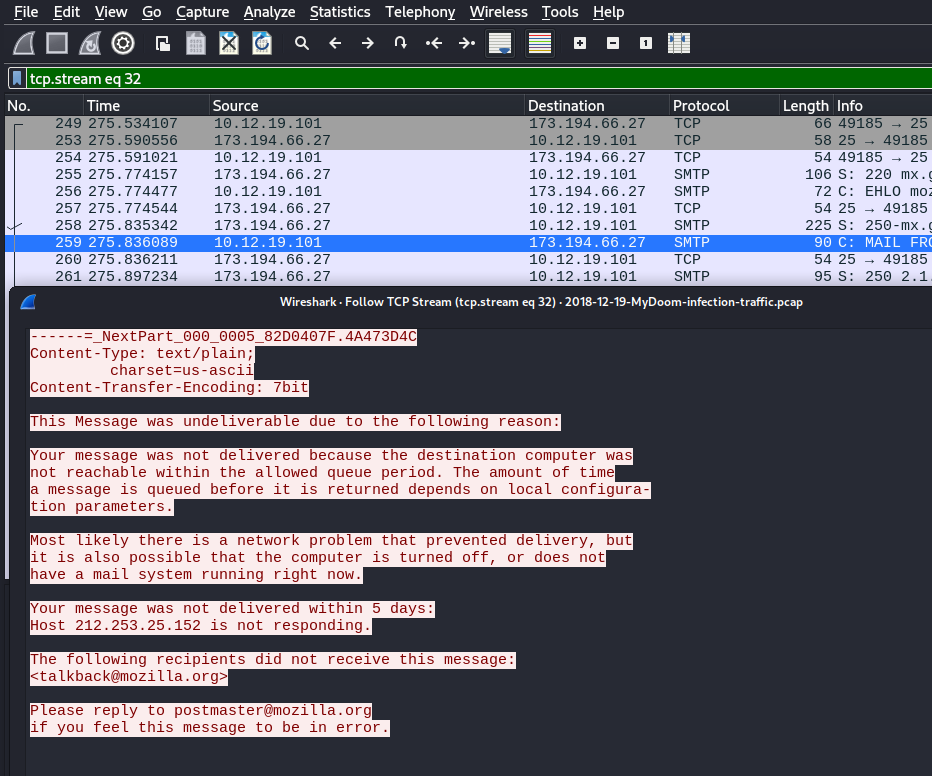
While malware-traffic-analysis.net often provides direct download links for the malware samples, I prefer a more hands-on approach—reconstructing them directly from the PCAP files.
In many cases, this can be as simple as using Wireshark’s "File > Export Objects" feature to retrieve transferred files.
Other times, extracting artifacts requires additional steps, such as decoding Base64-encoded payloads embedded in HTTP or SMTP traffic.
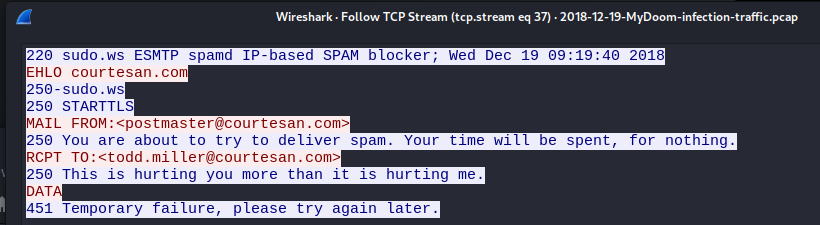
These traffic captures not only reveal malware behavior but also provide insight into how mail servers handle spam. In the example below, an infected machine (red) attempts to deliver spam emails but encounters an SMTP blackhole server (blue), which is designed to stall the worm. By responding with a 451 temporary failure code, the server tricks the worm into retrying later, effectively wasting its time.